How to use your Static Residential Proxies?
Configure Your Proxies
We support Static Residential Proxies authentication via Username/Password. You may check the Authentication Methods documentation to familiarize yourself with the concept.
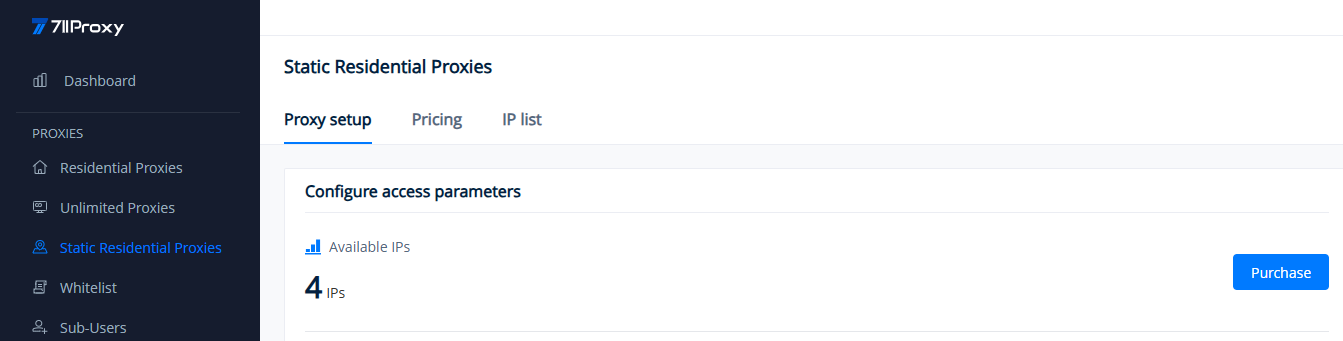
To configure your proxies, kindly navigate to the Static Residential Proxies > Proxy Setup section of your dashboard. The "Available IPs" section displays your current available IPs within the valid period.
Next, we will walk you through the proxy configuration method for Username/Password, with detailed screenshots and clear instructions.
Please note that the purchased static residential proxy IP addresses must be authenticated by the user to generate a proxy string for use. Entering the IP address directly into an application or tool will not work.
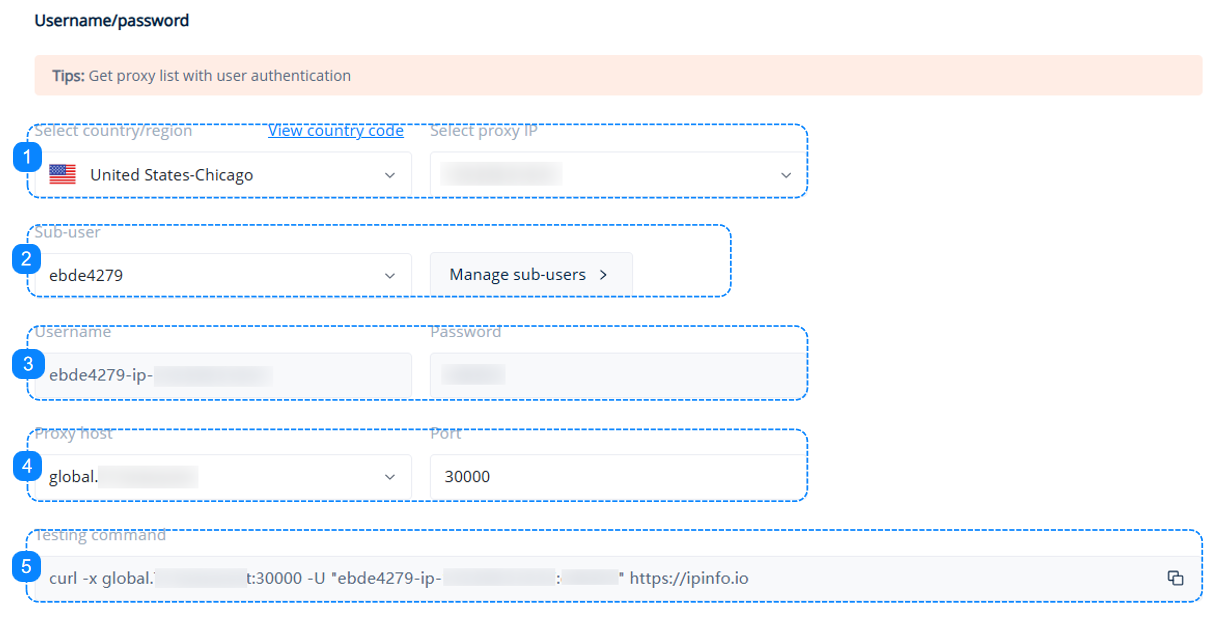
1. The "Select country/region" field only shows the available proxy locations for your current account. After you choose a country/region, the "Select Proxy IP" field will display the IP addresses corresponding to the selected country.
2. Choose the sub-user that will be accessing your proxies, or click on the "Manage Sub-users" button to create one. You may check our quick guide to Sub-Users.
3. Here you will find the username and password information for your chosen sub-user, these are the credentials that you will use to access your proxies.
4. Choose your proxy host. You may learn more on the Host and Port page.
5. The Testing Command is a cURL example which you can paste into your command line to quickly test your proxy settings. You may learn more on the Testing Command page.
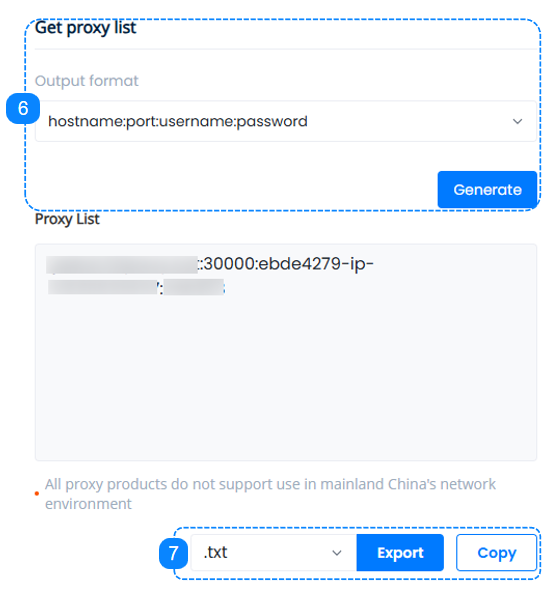
6. Here comes the essential step, on the right-hand side under "Get Proxy List", set up the correct format that suits our target and click on the "Generate" button, we can see the specifics reflecting the selections made above in the Proxy List, you may learn more on the Proxy String page.
7. Once you have configured your proxies, you are all set to start using them. Here we can either copy the generated proxy strings to the clipboard, or download them as a .TXT file or a .CSV file, which you can then apply to your software application or tool of choice.
When setting up your proxies on a browser extension, it is recommended to use the HTTP protocol, rather than SOCKS5.
The anti-detect browser can support HTTP or SOCKS5 protocols.
If you need more information on proxy integration with browsers, proxy managers, tools, etc., please refer to the quick guides in the Integrations section.
Was this helpful?